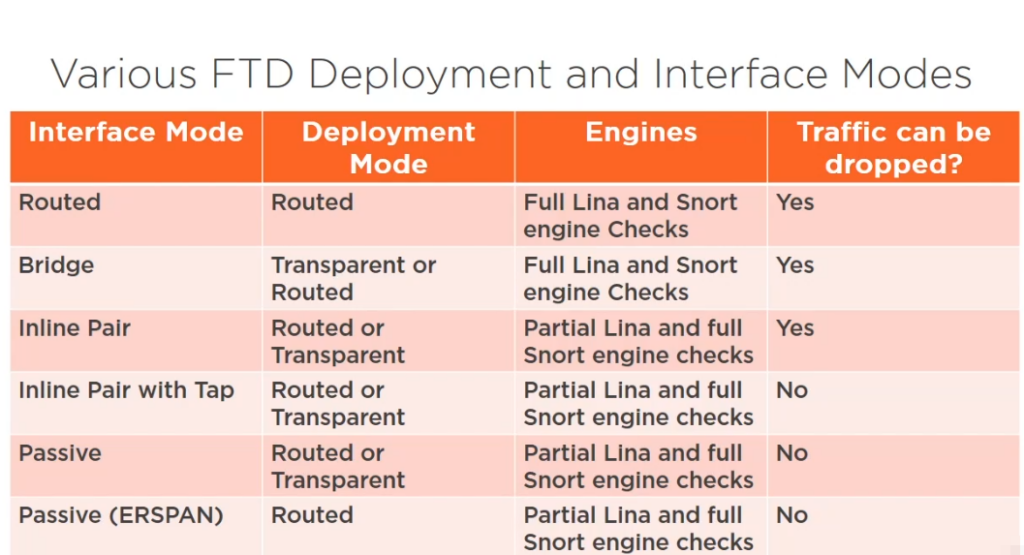
Cisco Firepower Threat Defense (FTD) is a unified software image that integrates firewall, intrusion prevention, and advanced threat protection capabilities. When deploying Cisco Firepower, understanding the interface modes and deployment options is critical for proper configuration and functionality. Below is an overview of Cisco Firepower deployment options and interface modes:
Cisco Firepower Deployment Options
Cisco Firepower can be deployed in various ways depending on the network architecture and security requirements:
- Routed Mode:
- The Firepower device acts as a Layer 3 router.
- Interfaces are assigned IP addresses and participate in routing.
- Suitable for deployments where the device needs to route traffic between different subnets.
- Supports dynamic routing protocols (e.g., OSPF, BGP).
- Transparent Mode:
- The Firepower device acts as a Layer 2 bridge.
- Interfaces do not have IP addresses (except for the management interface).
- Traffic is forwarded based on MAC addresses, making it invisible to the network.
- Ideal for deployments where the device needs to be inserted into an existing network without reconfiguring IP addressing.
- Inline Mode:
- Used for intrusion prevention and advanced threat detection.
- Traffic flows through the Firepower device, which inspects and enforces policies.
- Can be deployed in both routed and transparent modes.
- Passive Mode (Tap Mode):
- The Firepower device monitors traffic passively by receiving a copy of the traffic (via a network tap or SPAN port).
- Does not enforce policies or block traffic.
- Used for monitoring and analysis purposes.
Interface Modes in Cisco Firepower
Interfaces on a Cisco Firepower device can be configured in different modes depending on the deployment scenario:
- Routed Mode Interfaces:
- Used in routed deployments.
- Each interface is assigned an IP address and acts as a gateway for the connected subnet.
- Supports features like NAT, VPN, and dynamic routing.
- Switched Mode Interfaces:
- Used in transparent mode deployments.
- Interfaces are part of a bridge group and operate at Layer 2.
- No IP addresses are assigned to the interfaces (except for the management interface).
- Inline Set Interfaces:
- Used for inline inspection and threat prevention.
- Traffic flows through a pair of interfaces (ingress and egress) for inspection.
- Can be used in both routed and transparent modes.
- Passive Interfaces:
- Used in passive (tap) deployments.
- Receives a copy of the traffic for monitoring and analysis.
- Does not actively participate in traffic forwarding.
- Management Interface:
- Dedicated interface for device management.
- Used for accessing the Firepower Management Center (FMC) or Firepower Device Manager (FDM).
- Must have an IP address configured.
Deployment Considerations
- High Availability (HA):
- Firepower supports HA deployments using active/standby or active/active configurations.
- Requires proper interface and failover configuration.
- Performance:
- Ensure the Firepower device is sized appropriately for the expected traffic volume and inspection requirements.
- Licensing:
- Verify that the appropriate licenses are in place for the desired features (e.g., threat prevention, URL filtering, malware protection).
- Management:
- Decide whether to use Firepower Management Center (FMC) or Firepower Device Manager (FDM) for centralized management.
Configuration Steps
- Choose Deployment Mode:
- Determine whether to deploy in routed, transparent, or inline mode.
- Configure Interfaces:
- Assign IP addresses for routed mode or add interfaces to bridge groups for transparent mode.
- Set Up Security Policies:
- Configure access control policies, intrusion policies, and other security features.
- Deploy Configuration:
- Apply the configuration to the Firepower device.
- Monitor and Maintain:
- Use FMC or FDM to monitor traffic, update signatures, and troubleshoot issues.
By understanding the deployment options and interface modes, you can effectively design and implement a Cisco Firepower solution tailored to your network’s security needs.
