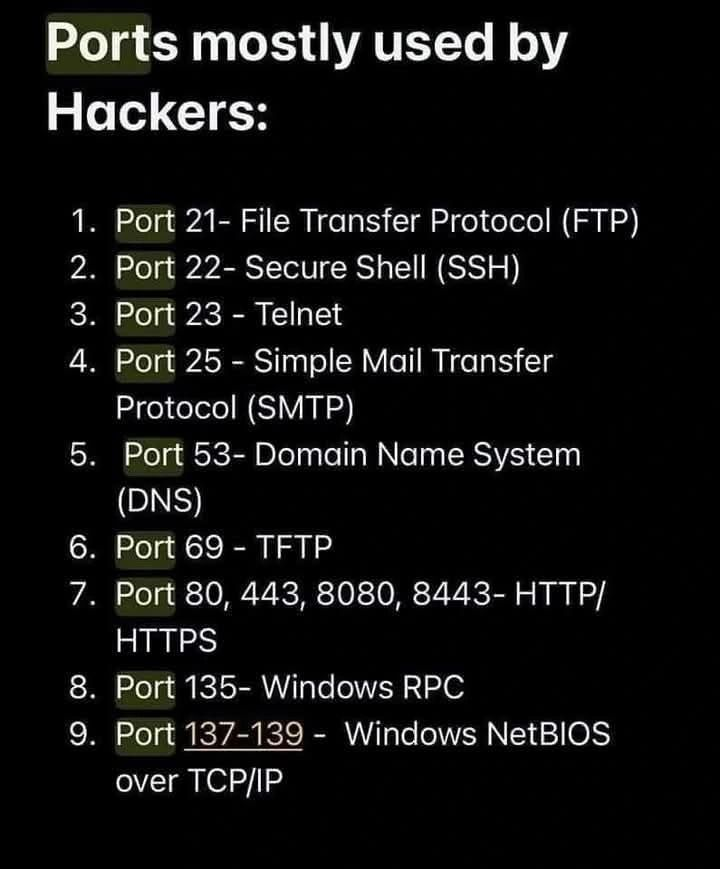
Network ports are essential communication endpoints that allow different services and applications to interact over a network. However, certain ports are frequently targeted by hackers due to their common use and potential vulnerabilities. Here’s a summary of the most commonly exploited network ports by hackers:
1. Port 20/21 (FTP – File Transfer Protocol)
- Used for file transfers.
- Vulnerable to brute-force attacks, anonymous authentication, and data interception.
2. Port 22 (SSH – Secure Shell)
- Used for secure remote access to systems.
- Targeted by brute-force attacks and credential stuffing.
3. Port 23 (Telnet)
- Used for remote access but transmits data in plaintext.
- Highly vulnerable to eavesdropping and credential theft.
4. Port 25 (SMTP – Simple Mail Transfer Protocol)
- Used for sending emails.
- Exploited for spam campaigns, phishing, and email spoofing.
5. Port 53 (DNS – Domain Name System)
- Used for resolving domain names to IP addresses.
- Targeted in DNS spoofing, cache poisoning, and DDoS attacks.
6. Port 80 (HTTP – Hypertext Transfer Protocol)
- Used for unencrypted web traffic.
- Exploited for web-based attacks like SQL injection, XSS, and phishing.
7. Port 110 (POP3 – Post Office Protocol)
- Used for retrieving emails.
- Vulnerable to brute-force attacks and data interception.
8. Port 135 (RPC – Remote Procedure Call)
- Used for inter-process communication.
- Exploited in worm propagation and remote code execution.
9. Port 139/445 (SMB – Server Message Block)
- Used for file and printer sharing.
- Targeted in ransomware attacks (e.g., WannaCry) and brute-force attempts.
10. Port 1433/1434 (Microsoft SQL Server)
- Used for database communication.
- Exploited for SQL injection and unauthorized access.
11. Port 3306 (MySQL)
- Used for MySQL database communication.
- Targeted in brute-force attacks and SQL injection.
12. Port 3389 (RDP – Remote Desktop Protocol)
- Used for remote desktop access.
- Exploited in brute-force attacks and ransomware campaigns.
13. Port 5900 (VNC – Virtual Network Computing)
- Used for remote desktop control.
- Vulnerable to brute-force attacks and unauthorized access.
14. Port 8080 (HTTP Alternate)
- Often used for web proxies or alternate HTTP services.
- Exploited for web-based attacks and unauthorized access.
15. Port 27017 (MongoDB)
- Used for MongoDB database communication.
- Targeted in brute-force attacks and data exfiltration.
Common Exploitation Techniques:
- Brute-Force Attacks: Hackers attempt to guess credentials by trying multiple username/password combinations.
- Man-in-the-Middle (MITM) Attacks: Intercepting and altering communication between two parties.
- Exploiting Vulnerabilities: Leveraging unpatched software or misconfigurations.
- Phishing and Social Engineering: Tricking users into revealing sensitive information.
Mitigation Strategies:
- Regularly update and patch software.
- Use strong authentication mechanisms (e.g., multi-factor authentication).
- Monitor and restrict access to sensitive ports.
- Implement firewalls and intrusion detection/prevention systems (IDS/IPS).
- Encrypt data in transit using protocols like TLS/SSL.
By understanding these commonly targeted ports and their associated risks, organizations can better secure their networks against potential cyber threats.
